Common Cyber-attacks in the U.S.
- Blog >
- Common Cyber-attacks in the U.S.
Cyber-attacks have risen worldwide, especially since the COVID-19 pandemic struck, with an increased number of companies suffering data breaches. According to Business Wire, 81% of organizations globally have experienced an increase in cyberthreats since the start of the pandemic. Much of this is due to the increase in work-from-home users and the expanded threat field that security teams must protect. Criminals took advantage of user anxiety to send suspected links and attachments that led to crucial data breaches.
Individuals and organizations remain susceptible to cyber-attacks targeting personal and corporate data. Here are some of the different cyber-attacks facing organizations today, especially U.S. organizations we’ve been talking to and working with.
Malware Attacks
Malware is a common form of a cyber-attack involving viruses and Trojans. Cybercriminals send code with malicious intent to steal data from an individual or organization, introducing it through email attachments, software downloads, or operating system vulnerabilities.
The Phorpiex botnet is the latest malware attack, and it’s rapidly spreading. The botnet spews spam at a high volume and delivers malware via phishing emails. After a malicious actor compromises a device on a network, they infect all the vulnerable devices on that network by spreading this malware across as many machines as possible, resulting in widespread damage that’s hard to control.
Phishing Attacks
Phishing is another common cybersecurity risk that became more sophisticated during the pandemic. This is where cybercriminals send links and attachments by email, directing a user to a dummy site. Phishing attacks function like spam but are more harmful to an organization.
For example, a botnet is the notorious email malware best spread through phishing. It’s a dangerous malware that seizes your computer’s control to send spam emails seeking to defraud unsuspecting victims. Malicious actors create these botnets to take advantage of unsecured internet of things (IOT), endpoint, and network devices and install malware that attacks the DNS servers as well as other outbound service devices that will ensure the success of their attacks.
DDOS Attacks
The denial-of-service attack, or DDOS, occurs when an attacker sends high volumes of data at a target with the intent of overloading the network to disrupt or stop operations completely. For example, a cybercriminal can use multiple computers to send traffic to a single destination device and cause it to become an overloaded system. They will then hijack that system or the network it is connected to, allowing them to steal vital information while the system is down or underperforming and your systems have to use a workaround to keep functioning.
The consequences of a DDOS attack can be devastating, including the risk of a complete shutdown. The use of a DDOS attack on critical environments like the Colonial Pipeline Ransomware Attack ensured that the multiple types of attack tactics used allowed for entry and then disbursement of the ransomware within that network. In this particular attack, the bad actors utilized a compromised credential (stolen password) to get into a system, but these kinds of attacks are commonly multifaceted to access sensitive systems, causing significant damage.
Password Attacks
This cyber-attack is common with personal devices like mobile phones and computers. It happens when a hacker cracks a password considered weak or unchanged for a long time. Attackers can easily access networks if there are simple passwords that are easy to infiltrate. The attackers use certain software to decrypt passwords when they are too weak. The password attack tactic allows a threat actor to obtain access to under-protected or weakly protected systems and then utilize them to further spread the attack they are perpetrating on this environment.
Protecting Against These Cyber-Attacks
There are several ways to respond to these common cybersecurity issues. Deploying robust and updated firewalls to prevent malware attacks seems like the most logical advice to offer. The implementation of a more extensive cybersecurity stack of tools is also a viable option. Organizations can mitigate cybersecurity attacks by implementing a firm password policy as well as a thorough Identity and Access Management (IAM) solution for multi-factor authentication to coincide with a strong password policy.
Most importantly though is the use of strong visibility, analytics, and identification solutions. Threats will expand every day. This being the case, the use of automation and asking less of your already overworked security analysts will ensure you are not missing vital event data that can help proactively respond to threats.
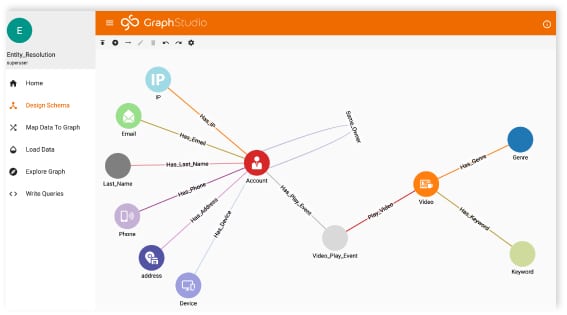
Graph technology allows you to bring the data from all of your disparate data sources together and ensure that they are being correlated properly while ensuring nothing is being passed up as a False Negative due to security tools not speaking to each other or sharing critical event data. TigerGraph allows you to ingest data across disparate tools to ensure you have the automated visibility, scanning, analysis, and threat identification to help quickly react to a threat within your environment.
End-user education and awareness will also help prevent these devastating attacks. Training employees to avoid clicking on links or downloading attachments from unsecured sources will ensure a higher probability of reduced successful phishing attacks. Employees are the last line of defense against cybersecurity threats – proactive awareness will help prevent these attacks.
Bottom Line
Cybersecurity threats are ever-present, with new vulnerabilities arising constantly. A secure online environment is needed to protect valuable information from cybercriminals and the visibility to be able to correlate events coming in at an astronomical rate is critical to the success of your security team.
Implementing security monitoring of networks and systems to mitigate cybersecurity liabilities is just the first step. Being able to analyze the enormous number of threats and events coming into those systems is what will save you in the end. Graph technology could make your analysis faster, more efficient, and more effective and ensures less human error or oversight due to exhaustion and alert fatigue. To learn more, reach out to TigerGraph and see how we can complement your existing cybersecurity stack to protect your environment.