Preventing Audit Log Data Breaches with Data Masking and Graph Deep Link Analytics
- Blog >
- Preventing Audit Log Data Breaches with Data Masking and Graph Deep Link Analytics
Log files contain sensitive data, making them a tempting target for cybercriminals. There have been several data breaches, some of them high profile, targeting log files that have resulted in millions of sensitive personal data records being exposed.
In 2018, for example, more than 330 million Twitter users were affected by a breach that exposed their passwords from an internal log. The attackers in the Twitter breach exploited a bug that caused passwords to be stored as readable text, making them easy to exploit.
With log files, particularly audit logs, holding such sensitive information, securing them against unauthorized access is crucial. The use of deep link analytics and threat analysis made possible with graph technology allows your security team to quickly identify the anomalous activity and react before a breach allows attackers to get control of your environment or begin data exfiltration.
What Are Audit Logs?
An audit log is a record of the events happening in a computer system. It contains restricted information such as passwords and IP addresses. The sequential logs and records become an audit trail that can be readily accessed by bad actors to find your sensitive or confidential data.
Audit logs, also known as bread crumbs, contain passwords, user names, credit card data, and other sensitive information. The data appears as plain text in log files and can cause significant damage if the data falls into the wrong hands. These logs either contain or point a bad actor to the sensitive systems and information they need or want to exploit.
Logs are essential in a system as they help improve security by detecting any unauthorized access. They also help system administrators to find and debug problems. However, audit files can be altered, corrupted, or even stolen by a bad actor, like any other files in your system. They contain sensitive data, making them a target for hackers or malicious insiders looking for a way to wreak havoc on your environment. The worst part of all is the majority of these logs and the respective data are stored in plain text making them much less secure.
Securing Audit Logs – Encryption
Encrypting your audit files ensures they’re protected on your servers and while in transit to a log collector or system analysis tool. Only users with the encryption certificate can access and view the audit logs.
Encryption on its own isn’t perfect. It’s also possible for hackers to compromise and access your encrypted files. In May 2021, hackers accessed Acer’s files and leaked images of sensitive financial spreadsheets and documents. If hackers obtain the encryption certificate or decryption key using tactics such as a “Man in the Middle” attack, your logs will no longer be protected. You must ensure that sensitive information is protected as soon as it appears in the audit file or while in transit.
Increasing Audit Log Security – Data Masking
As information in log files is stored in plain text and can be accessed with a description key, the best way to protect it is by masking the data at the source.
Data masking, also referred to as data anonymization or data obfuscation, replaces sensitive data with fictitious functional data like characters, data scrambling, substitution, and shuffling, among others. The goal is to create a version of the data that cannot be decrypted or deciphered.
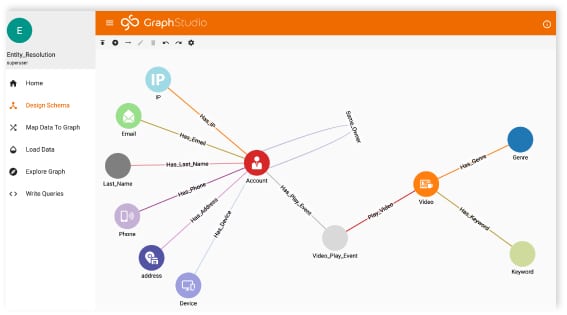
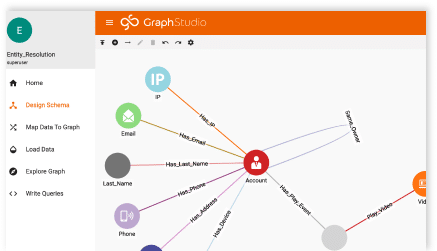
Masking the data at the source — instead of the server — ensures all the sensitive data entered at the source, such as private keys and passwords, are protected. The actions taken by a bad actor would set off a notification of anomalous activity, and with the deep link analytics and in-database machine learning with TigerGraph, we can easily help you be much more proactive while analyzing and reacting to threats.
Some compliance regulations require you to keep your audit logs for a particular duration. The longer you retain them, the more the risk of exposure. Masking the data will help you keep the logs secure as long as you’re required to keep them. Constant analysis of the data stored for set periods of time will also ensure you are proactively watching for any type of inappropriate action taken either by an insider threat actor or external bad actor attempting to access the sensitive data within your logs.
In a world of relentless cyberattacks and data breaches, you must secure your data. Audit logs help organizations manage security and risk, but sensitive and confidential information is at risk when they’re compromised. The best solution is to mask your data to prevent unauthorized parties from accessing and viewing them unexpectedly.
Implement True Graph Analytics to Ensure Proactive Threat Analysis
With the never-ending alerts, events, activity notices, remote workers, partner access, and many other forms of risk within your environment, cyberattacks, and data breaches are becoming more difficult to identify. The in-database machine learning, connected data analysis, deep link analytics, and overall centralized viewpoint offered by TigerGraph’s graph analytics will enable your SOC and NOC analysts with the most comprehensive review and automation on the market.
If you’d like to learn more about deep link analytics, I recommend reading this white paper written by our CEO, Yu Xu. And, of course, we are available to discuss your graph analytics and cybersecurity needs.