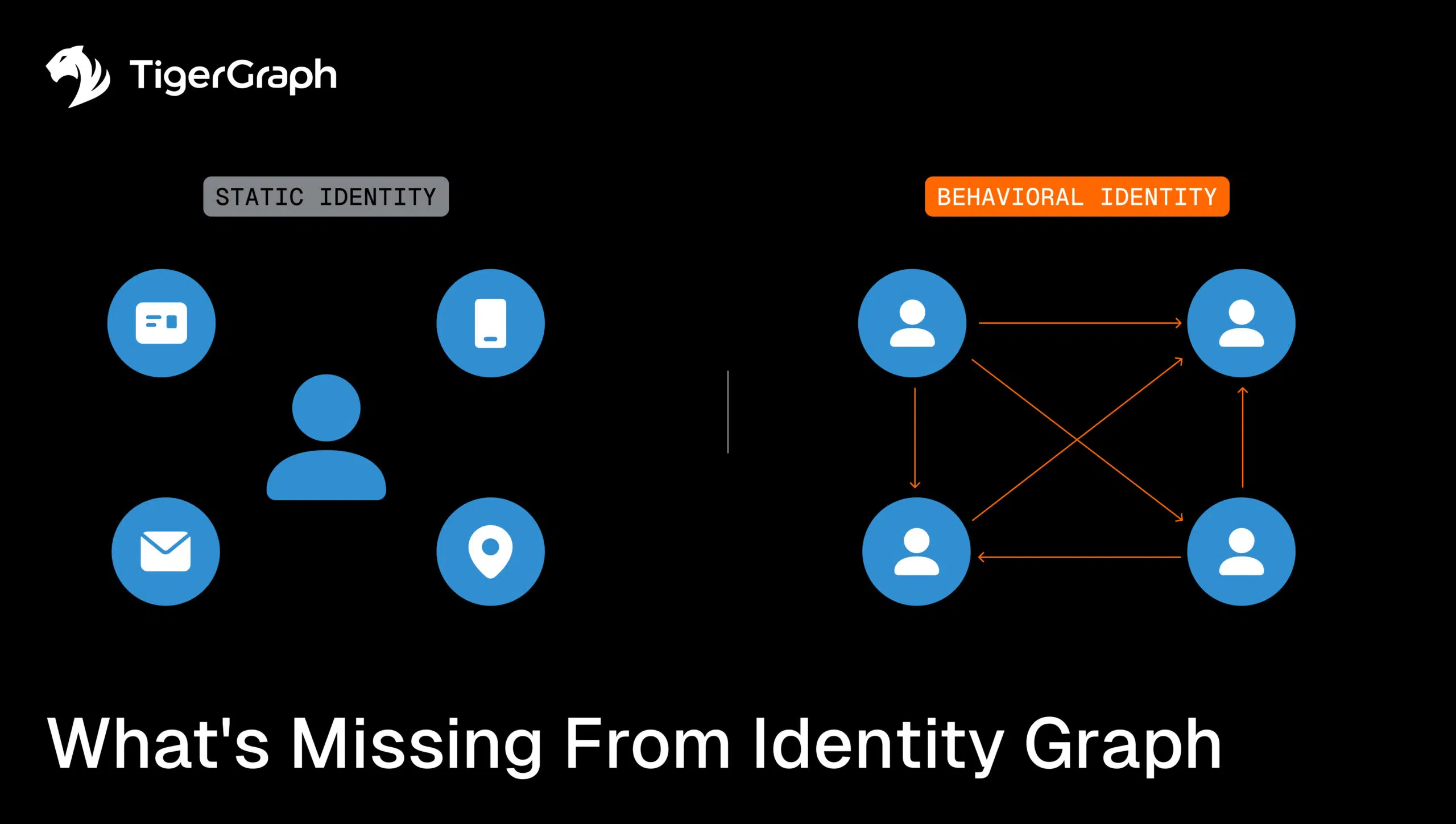
What’s Missing from Your Identity Graph? Behavior.
Behavior is the missing layer in most identity graphs, especially when it comes to financial crime and AML/KYC programs. Although banks have unified names, addresses, and device IDs into consolidated profiles, what they often lack is the dynamic activity that exposes risk in real time.
Forward-thinking businesses are using graphs to perform identity resolution in banking, the customer record matching that is essential for customer 360, personalization, compliance, and fraud detection with identity graph analytics. Dynamic identity resolution has become the cornerstone of modern fraud detection, KYC, and AML programs. For banks, an identity graph in banking that includes behavior is critical for staying ahead of fraudsters.
Banks have invested millions into building “identity graphs” that unify customer attributes, including names, addresses, emails, phone numbers, and device IDs, into a single profile. This consolidation was an essential step forward. It allowed institutions to collapse duplicate records, flag synthetic identities built from mismatched data, and reduce onboarding friction for legitimate customers.
But unfortunately, most identity graphs stop there. They unify static attributes, but they don’t capture the dynamic behaviors that reveal fraud as it unfolds. A mule account looks legitimate on paper. A synthetic ID passes the attribute check. A merchant onboarding request matches a plausible business address. The static data isn’t what makes them suspicious; it’s the patterns of activity and connections over time.
Without behavioral linking, an identity graph is essentially a frozen snapshot. It’s useful for cleaning up records, but blind to how fraud actually unfolds. The gaps fraudsters exploit are almost always revealed in movement and relationships:
• Accounts that transact with each other more often than chance would allow.
• Devices that log into multiple, seemingly unrelated profiles.
• Merchants that consistently appear at the center of chargeback clusters.
• IP addresses that bounce between identities in multiple jurisdictions.
These are exactly the blind spots regulators warn about. Without behavioral identity resolution banks remain vulnerable in AML and KYC compliance.
An attribute-only identity graph will miss these because it lacks a memory of when, how often, and with whom entities interact. That means fraud teams end up reacting after the losses, instead of seeing the network form before it strikes.
In short, what’s missing is behavior. And without it, identity resolution stops short of its true purpose—turning static data into living intelligence that can keep pace with fraud in motion.
Why Behavior Matters in Identity Resolution
Behavior isn’t an optional layer on top of identity resolution in banking, but the context that makes an identity graph useful for fraud detection with identity graph methods. Three forces make this especially urgent for top banks today:
- Fraud is networked action, not individual states.
Modern fraud schemes are designed to pass basic attribute checks. A synthetic identity may have a real SSN paired with a fake address; a mule account may look indistinguishable from a legitimate customer profile. What exposes them is the web of interactions:
- Multiple accounts funneling small-dollar transactions through the same device.
- “First-use” credit cards that immediately transact at the same set of risky merchants.
- Dormant accounts that suddenly activate in coordinated bursts.
These patterns are invisible when records are flattened into rows. But they light up in a behavioral identity graph that records the interactions as well as the objects.
- Regulators demand explainable context.
Compliance frameworks like AML, KYC, and FinCEN’s new priorities increasingly require why an account was flagged, not just that it was. Behavioral linking provides this lineage, a critical aspect of behavioral data for AML and KYC audits. Banks can demonstrate, for example:
- A new account was three hops away from a confirmed fraud ring.
- A device fingerprint was reused across five identities tied to prior SARs.
- A set of merchants processed overlapping transactions in the same five-second window.
This creates audit-ready transparency, which regulators expect and which static identity resolution cannot deliver.
- Customers demand speed and fairness.
False positives erode trust and send good customers to competitors. Behavioral linking makes it possible to separate legitimate anomalies from truly suspicious activity.
- A frequent traveler setting off location alerts looks risky in isolation, but becomes safe when contextualized with a long-standing travel pattern.
- Family members sharing a tablet may trigger duplicate-device warnings, but with behavioral analysis, those patterns clearly differ from mule account behavior.
By adding behavior, banks can approve legitimate activity faster while focusing investigator attention on actual risk. That’s why banks are adopting graph-powered fraud prevention, reducing false positives while improving customer experience.
How TigerGraph Elevates Identity Graphs
While traditional tools flatten data into rows, TigerGraph makes relationships and behavior first-class citizens.
- Entity Resolution + Behavior: Connect fragmented records into a unified identity graph in banking and layer in how those identities transact, log in, and interact, enabling dynamic identity resolution..
- Multi-hop Analysis: Detect when a new applicant is two steps from a fraud ring, or when multiple accounts converge on the same device. This is the power of fraud detection with identity graph analytics.
- Explainable AI Integration: Feed graph-derived behavioral features—community membership, transaction cadence, anomaly scores—directly into ML pipelines, producing predictions regulators can understand.
- Enterprise-Scale Proof: TigerGraph runs at the scale of top-tier banks, powering millions of transactions per day, sub-ms queries, hundreds of millions in annual savings.
Real-World Example: At one leading digital bank, identity resolution alone wasn’t catching scam networks. By layering in behavioral context, such as device reuse, temporal patterns, and shortest-path proximity to known mule accounts, the bank significantly increased fraud recall, while also cutting false positives. This resulted in millions of monthly losses prevented, faster investigations, and stronger protection for customers—showing the power of behavioral identity resolution at scale. And it was all possible without adding headcount.
An identity graph without behavior is like a map without roads. You can see the landmarks, but not how they connect or where the traffic is flowing. TigerGraph combines entity resolution with behavioral linking and context, giving banks and other businesses the ability to expose fraud rings, meet compliance demands, and protect customers in real time.
This is just one example of how graph-powered fraud prevention and dynamic identity resolution strengthen financial crime defenses while improving customer trust.
Ready to see the full picture? TigerGraph can help you build identity intelligence that scales with your business and outpaces fraudsters. Reach out to learn more today.